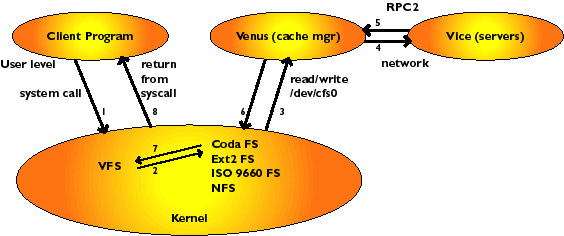
Figure 3 - Client / Venus / Vice Diagram17
3.2.2 CODA
CODA is a distributed file system similar to the types already in existence like NFS. CODA is developed by the Computer Science Department at Carnegie Mellon University. In the CODA HOWTO the description of the system is given as:
"...a distributed file system, i.e. it makes file available to a collection of client computers as part of their directory tree, but ultimately maintains the authoritative copy of the file data on servers."16

Figure 3 - Client / Venus / Vice Diagram17
CODA not only provides the remote access of files but also these important attributes, which I will comment on each in turn:
Mobile clients properties:
"Reintegration of data from disconnect clients"18
Disconnected operations from mobile clients may not be proper with a server farm where this project might typically reside. Yet reality tells that even with fixed networks there can be problems the typically can cause interruption of network services. It would be important that if a segment of the server farm where taken down for maintenance that it would be synchronized on reinsertion.
"Bandwidth adaptation"19
Venus, the CODA program used on user systems to connect with the Vice servers, has the ability to monitor the network properties (i.e. bandwidth rate). It can then adapt itself to the loading in the network and change its time between synchronization. It can operate in its normal fully connected mode or by its weakly connected mode. The fully connected mode maintains high consistency between the files. If the target programs being compiled on the DGCC system need to be updated as quickly as they are completed to maintain synchronization between the various client Venus systems and the main Vice servers where the files actually exist. If this is not done then the system will fail to compile and its performance will be significantly degraded. The weakly connected mode would not be a recommend method since it provides improved performance but not the same guarantee as fully connect mode for file consistency.
"Failure Resilience:"20
Read / write replication servers21
The CODA system has the ability to have primary and secondary servers. As data is written to the primary server its also copied to the secondary servers. In the case of failure of the primary server the work can continue. This is important when considering the typical server farm does not run without some sort of problem during normal operation.
Mobile client and failure resilience properties are vital to the performance of this project. Compilations cannot be interrupted, lost or corrupted. The target project being worked on should exist on more than one Vice server thereby providing redundancy and removing the failure due to having a single point of failure. If the main Vice server goes down a backup server should pickup without any notice to operation. Network failures are a part of life but the design feature of this system is to prevent the interruption of the service. CODA was designed to overcome this typical problem for normal desktop and mobile computer users.
Performance and scalability:22
Client side persistent caching of files, directories and attributes for high performance23
Each Venus client holds a small cache of recently accessed files. This helps by eliminating unnecessary resending of files that already exist locally. Vice servers also have the ability add new servers into the server without interruption. New servers can be synchronized quickly thereby returning damaged systems to service or adding new servers to handle existing system load.
Security:
Kerberos like authentication
Kerberos uses tickets to authenticate users to various services. CODA uses a similar style of authentication. When a coda client logs into the service it obtains a token (similar to tickets) for the user. This token is then used for authenticating any action taken on the behalf of the user. For example, writing to a directory, etc.
Access control lists (ACLs)
Security is something that should be forgotten. It often is after thought put in after a customer requires it. CODA provides security through the use of kerberos-like-authentication using tokens to validate a Venus client accessing a Vice server. Also through the use of access control lists users can be group into various projects so that authorized people are the only ones allowed to write to a directory for example. This project has always held the view that security cannot and must be ignored. Unless a project is designate to be open source, like this project, it will be critical that the data be protected from prying eyes. Unless someone has access via the access control list they cannot view any data on CODA servers. This is one method of protection but it is vulnerable to man in the middle attack since the data is not encrypted when in transit between systems.
By using CODA instead of developing a method for transferring files between systems saved enormous amount of time. Without CODA this project could not have reached the goal of a working proof of concept within the time allowed.
| Previous: Chapter 3 - Background On Related Technologies | Home | Next: Chapter 3 - Other Technologies |